Do you need to know what your child is doing on the computer? Do you
need to monitor what your employees are doing during work hours? Is
someone tampering with your computer while you are away?
WinSpy is a Complete Stealth Monitoring Software that can both monitor
your Local PC and Remote PC. Win Spy Software operates in stealth mode.
Win-Spy will not show in Add/Remove Programs, Windows Start, Taskbar,
Task Manager, Processes or in Program Files Folder. Win-Spy can either
be used for you Home or Office.
Win-Spy is a complete Local and Remote monitoring package with following things :
- Screen Capture
- WebCam Shots
- Reports - Keylog
- Chat Conversation
- Website Visited Detail
- Website Visited Summary
- Restricted Sites Visited
- Time Spent Online
- PC Activity
- Anti Spyware
- Login Attempts
- PC Usage or Active Time
- Lost Stolen PC Location
- Emailer for Keylog, Screen Capture and Reports
- Streaming Web-Cam (View / Record)
- Remote Mic (Record / Listen)
- Remote PC file Browser and FTP
- Remote PC file Download / Uploader / Execute / Delete
- Remote PC Shutdown / Log Off
- Send Message to Remote PC
- Anti-Spy Disable / Destroy
- Anti Virus Stealth Technology
- 3 remote file deployment - combine, exe and excel
- 3 ways to obtain remote information - email, direct connect, ftp
- 3 methods to for remote uninstall - auto, direct connect, via uninstall file
- Monitor up to 10 remote PC with 49.95 version
- Suspend on Idle
- Centralized Monitoring
- Save information across network
- Works even with Firewall / Router
- WebAccess
- FTP Reports/Screen Shots/Cam Shots to My PC
- Remote Desktop Connect to Remote
Keylogger is an efficient password stealer software used for hacking
various email account password such paypal password hacking, facebook
password hacking etc. I have already explained on wildhacker about RATs
and keyloggers to hack various email account passwords, where you have
to send your keylogged file to victim. I have provided link for Winspy
keylogger software download. Using winspy keylogger you can easily hack
or steal the password of Twitter account, Facebook Account, Gmail
Account, Hotmail Account, Yahoo Accounts and many other account password
easily.
Basically, in this trick you create server file which is used to capture
the keystrokes of your slave, after creating server file you have to
send that file to slave and use a bit of social engineering to get them
to click on the server file and run the server file. Once the server
file is run, it will start his working like capturing keystrokes etc.
How To Hack Facebook / Gmail Password Using Winspy keylogger
Step 1: First of all download Winspy keylogger software from link given below:
Step 2: After downloading,
run the myspace password hacking software. On running, a dialog box will
be prompted. Now, create an userid and password on first run and hit
apply password. Remember this password as it is required each time you
start Winspy and even while uninstalling.
Step 3: Now, another box
will come, explaining you the hot keys(Ctrl + Shift + F12) to start this
Winspy keylogger software to hack myspace account password.
Step 4: Now, on pressing hot keys, a login box will come asking userid and password. Enter them and click OK.
Step 5: Now, Winspy’s main screen will be displayed as shown in image below
Step 6: Select Remote at top, then Remote install.
Step 7: On doing this, you will get a popup box as shown in image. Now, fill in the following information in this box.
Thats it friends..........
So guys, I hope you have got the trick on how to
Hack Facebook Paypal Twitter Gmail Account Password Using Winspy
keylogger. Winspy keylogger is widely used to hack myspace account
passwords. If you have any problem in using this myspace hacking
software to hack myspace account password, feel free to mention it in
comments section.
 Posted in: fake call
Posted in: fake call Posted in: Crypter
Posted in: Crypter Posted in: Keylogger
Posted in: Keylogger Posted in: Keylogger
Posted in: Keylogger
 Posted in: Crypter
Posted in: Crypter Posted in: Crypter
Posted in: Crypter Posted in: Crypter
Posted in: Crypter Posted in: web Hacking tools
Posted in: web Hacking tools Posted in: Binder
Posted in: Binder Posted in: stealer
Posted in: stealer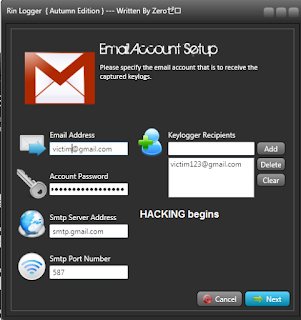
 Posted in: Keylogger
Posted in: Keylogger Posted in: Keylogger
Posted in: Keylogger Posted in: sms bomber
Posted in: sms bomber





